Based azure security best practices: Top 7 Ultimate Based Azure Security Best Practices for 2024
In today’s cloud-driven world, mastering based azure security best practices isn’t optional—it’s essential. From startups to enterprises, securing your Azure environment starts with proven strategies that protect data, identity, and infrastructure. Let’s dive into the most effective, up-to-date methods to lock down your cloud.
1. Implement Identity and Access Management with Zero Trust Principles

One of the most critical based azure security best practices is establishing a robust identity and access management (IAM) framework grounded in Zero Trust. In Azure, identity is the new perimeter. Without strict control over who or what can access resources, even the most fortified network means little.
Use Azure Active Directory (Azure AD) for Centralized Identity Control
Azure AD is the cornerstone of identity management in Microsoft’s cloud ecosystem. It enables single sign-on (SSO), multi-factor authentication (MFA), and conditional access policies across all Azure services and integrated third-party applications.
- Enforce MFA for all users, especially administrators.
- Leverage Azure AD Identity Protection to detect risky sign-ins and automate responses.
- Use Identity Governance to manage access reviews and entitlement management.
According to Microsoft, organizations that enable MFA block over 99.9% of account compromise attacks (Microsoft Security Blog).
“In a Zero Trust model, trust is never assumed, regardless of network location.” — Microsoft Zero Trust Model
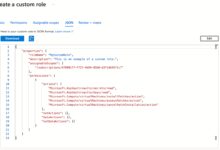
Apply the Principle of Least Privilege (PoLP)
Assign users and services only the permissions they need to perform their tasks—no more, no less. Azure Role-Based Access Control (RBAC) allows granular permission assignment.
- Avoid using built-in roles like Owner or Contributor globally; instead, create custom roles with minimal required actions.
- Regularly audit role assignments using Azure AD Access Reviews.
- Use Just-In-Time (JIT) access via Azure Privileged Identity Management (PIM) to limit standing privileges.
For example, a developer may need read/write access to a specific storage account but shouldn’t have permissions to modify network configurations. Enforcing PoLP reduces the attack surface significantly.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
2. Secure Azure Network Architecture with Defense-in-Depth
Network security remains a foundational element of based azure security best practices. A well-architected network minimizes exposure to threats and ensures traffic flows securely between resources.
Design with Azure Virtual Networks and Subnets
Azure Virtual Networks (VNet) provide isolated environments for your resources. Segmenting your network using subnets enhances security by limiting lateral movement in case of a breach.
- Separate subnets by function (e.g., web, app, database).
- Use Network Security Groups (NSGs) to control inbound and outbound traffic at the subnet or NIC level.
- Implement service endpoints or private endpoints to secure connections to PaaS services like Azure Storage or SQL Database.
Private Link, for instance, allows you to access Azure services over a private IP address, eliminating exposure to the public internet (Microsoft Learn: Azure Private Link).
Deploy Azure Firewall and Web Application Firewall (WAF)
Azure Firewall is a managed, cloud-native firewall service that provides high availability and scalability. It filters traffic based on application FQDNs, network addresses, and ports.
- Use Azure Firewall to enforce outbound internet access policies.
- Integrate with Azure Firewall Manager for centralized policy management across multiple VNets.
- Enable WAF on Azure Application Gateway to protect web apps from common threats like SQL injection and cross-site scripting (XSS).
WAF policies can be customized using predefined rule sets (e.g., OWASP Core Rule Set) and can operate in detection or prevention mode.
“Network segmentation and traffic filtering are critical to preventing lateral movement in cloud environments.” — NIST SP 800-125B
3. Harden Azure Compute Resources Against Threats
Compute instances—such as Virtual Machines (VMs), containers, and serverless functions—are common targets for attackers. Applying based azure security best practices to these resources is vital for maintaining a secure posture.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
Secure Azure Virtual Machines with Azure Security Center
Azure Security Center (now part of Microsoft Defender for Cloud) provides unified security management and advanced threat protection across hybrid cloud environments.
- Enable continuous vulnerability scanning for VMs.
- Apply security recommendations like enabling disk encryption or installing endpoint protection.
- Use JIT VM access to restrict RDP/SSH access to approved requests only.
Defender for Cloud also offers adaptive application controls, which learn normal process behavior and block unauthorized executables.
Protect Container Workloads in Azure Kubernetes Service (AKS)
As container adoption grows, so does the need to secure them. AKS integrates with Defender for Containers to provide runtime protection, image scanning, and threat detection.
- Scan container images in Azure Container Registry (ACR) for vulnerabilities before deployment.
- Use pod security policies (or Azure Policy for Kubernetes) to enforce security baselines.
- Enable Defender for Containers to detect crypto-mining, command-and-control (C2) communications, and privilege escalation attempts.
For example, misconfigured Kubernetes pods with excessive privileges can be exploited to gain cluster-wide access. Enforcing least privilege at the pod level mitigates this risk.
4. Encrypt Data at Rest and in Transit
Data protection is a cornerstone of based azure security best practices. Whether stored in databases, blobs, or backups, sensitive information must be encrypted both at rest and in transit.
Use Azure Disk Encryption for VMs
Azure Disk Encryption leverages the industry-standard BitLocker (Windows) and DM-Crypt (Linux) to encrypt OS and data disks.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
- Integrate with Azure Key Vault to manage encryption keys and secrets.
- Ensure Key Vault access policies are tightly controlled and audited.
- Use customer-managed keys (CMK) instead of platform-managed keys for greater control.
Encryption keys should be rotated regularly, and access should be logged for compliance auditing.
Enable Transport Layer Security (TLS) Across Services
All data moving between clients and Azure services—or between services—should be encrypted using TLS 1.2 or higher.
- Enforce HTTPS for Azure App Services and Storage Accounts.
- Disable outdated protocols like TLS 1.0 and 1.1 using Azure Policy.
- Use Azure Front Door or Application Gateway to terminate TLS and offload encryption processing.
Microsoft recommends disabling legacy TLS versions to prevent vulnerabilities like POODLE or BEAST (Microsoft TLS Guidance).
“Encryption is not optional—it’s a baseline requirement for data protection in the cloud.” — GDPR, HIPAA, and CCPA Compliance Frameworks
5. Monitor, Detect, and Respond with Azure Sentinel and Defender for Cloud
Proactive threat detection and rapid response are key components of based azure security best practices. Reactive security is no longer sufficient in today’s threat landscape.
Leverage Microsoft Defender for Cloud for Unified Security Management
Defender for Cloud provides a centralized dashboard for security posture management, threat protection, and compliance monitoring.
- Enable Defender’s cloud workload protection plan for servers, containers, and databases.
- Review security recommendations and remediate issues like unencrypted storage or open firewall rules.
- Use secure score to measure and improve your security posture over time.
The secure score quantifies your environment’s security level and provides actionable steps to improve it—making it easier to prioritize efforts.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
Deploy Azure Sentinel for Advanced Threat Hunting
Azure Sentinel is a cloud-native Security Information and Event Management (SIEM) solution that uses AI and automation to detect and respond to threats.
- Connect data sources like Azure AD logs, VM logs, and firewall logs.
- Create custom detection rules using Kusto Query Language (KQL).
- Automate incident response with playbooks powered by Logic Apps.
For instance, you can create an alert that triggers when multiple failed login attempts are followed by a successful sign-in from a new location—indicative of a brute-force attack.
“Azure Sentinel enables organizations to detect threats 60% faster than traditional SIEMs.” — Microsoft Case Studies
6. Enforce Compliance and Governance with Azure Policy
Scaling security across large Azure environments requires automation and consistency. Azure Policy is one of the most powerful based azure security best practices for enforcing organizational standards and regulatory compliance.
Apply Built-in and Custom Security Policies
Azure offers hundreds of built-in policies for security, such as “Deploy Diagnostic Settings” or “Monitor Unattached Disks.”
- Assign policies at the management group, subscription, or resource group level.
- Use policy initiatives (like the “Azure Security Benchmark”) to bundle related policies.
- Create custom policies to enforce internal standards (e.g., tagging requirements or region restrictions).
Policies can be set to “Audit” mode to assess compliance or “Deny” mode to block non-compliant resource creation.
Integrate with Regulatory Compliance Standards
Azure Policy includes compliance packages aligned with standards like ISO 27001, NIST 800-53, HIPAA, and GDPR.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
- Use the Regulatory Compliance dashboard in Azure Security Center to track adherence.
- Generate compliance reports for auditors.
- Remediate non-compliant resources using automated remediation tasks.
This integration simplifies compliance efforts and reduces manual overhead.
7. Backup, Recover, and Test Resilience Regularly
No security strategy is complete without a robust disaster recovery and backup plan. Based azure security best practices include ensuring data availability and integrity during outages or ransomware attacks.
Use Azure Backup for Reliable Data Protection
Azure Backup provides scalable, encrypted, and managed backup solutions for VMs, files, and databases.
- Configure backup policies with retention periods aligned to business needs.
- Enable soft delete to protect backups from accidental or malicious deletion.
- Store backups in a different region for geo-resilience.
Backups are encrypted using Microsoft-managed or customer-managed keys, ensuring data confidentiality.
Test Disaster Recovery with Azure Site Recovery
Azure Site Recovery (ASR) enables replication of on-premises and Azure VMs to a secondary region.
- Define recovery plans with correct boot order and network mapping.
- Conduct regular failover drills without impacting production.
- Monitor replication health and RPO/RTO metrics.
Regular testing ensures that your recovery process works when needed most—during an actual incident.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
“Organizations that test disaster recovery plans are 3x more likely to recover successfully from ransomware.” — Microsoft Digital Defense Report 2023
What are the most critical based azure security best practices?
The most critical based azure security best practices include enforcing least privilege access via Azure AD and RBAC, encrypting data at rest and in transit, using Azure Firewall and WAF for network protection, enabling Microsoft Defender for Cloud, and implementing automated compliance with Azure Policy.
How do I secure Azure Virtual Machines?
To secure Azure VMs, enable Azure Disk Encryption, install endpoint protection, apply security patches regularly, restrict access using NSGs and JIT, and monitor for threats using Microsoft Defender for Servers.
What is the role of Azure Sentinel in cloud security?
Azure Sentinel acts as a cloud-native SIEM that collects logs, detects threats using AI, and automates responses with playbooks. It provides visibility across hybrid environments and accelerates incident response.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
How can I ensure compliance in Azure?
You can ensure compliance by using Azure Policy to enforce security standards, leveraging built-in compliance benchmarks, and utilizing the Regulatory Compliance dashboard in Microsoft Defender for Cloud to track alignment with standards like GDPR or HIPAA.
Is Zero Trust achievable in Azure?
Yes, Zero Trust is fully achievable in Azure by implementing strict identity verification, least privilege access, micro-segmentation, continuous monitoring, and encryption. Microsoft’s Zero Trust architecture guide provides a clear roadmap for implementation.
Securing your Azure environment requires a proactive, layered approach grounded in based azure security best practices. From identity and network security to threat detection and disaster recovery, every layer matters. By leveraging tools like Azure AD, Defender for Cloud, Azure Policy, and Sentinel, organizations can build a resilient, compliant, and secure cloud infrastructure. The key is consistency, automation, and continuous improvement—because in cybersecurity, standing still means falling behind.
based azure security best practices – Based azure security best practices menjadi aspek penting yang dibahas di sini.
Further Reading: